In real work operation, supporting millions of banking transactions a month, one of our customers migrated from an active face liveness technique to ID R&D passive liveness, and completion rates increased from 60% to 95%+. This was in one of the more challenging production environments with a very wide range of operating parameters.
On the back of the improved liveness success rates experienced (faster, more accurate, much higher completion rates with much less attempts) the customer expanded their use of the system and their business dependency on ID R&D liveness for a much broader digital engagement on a long-term basis.

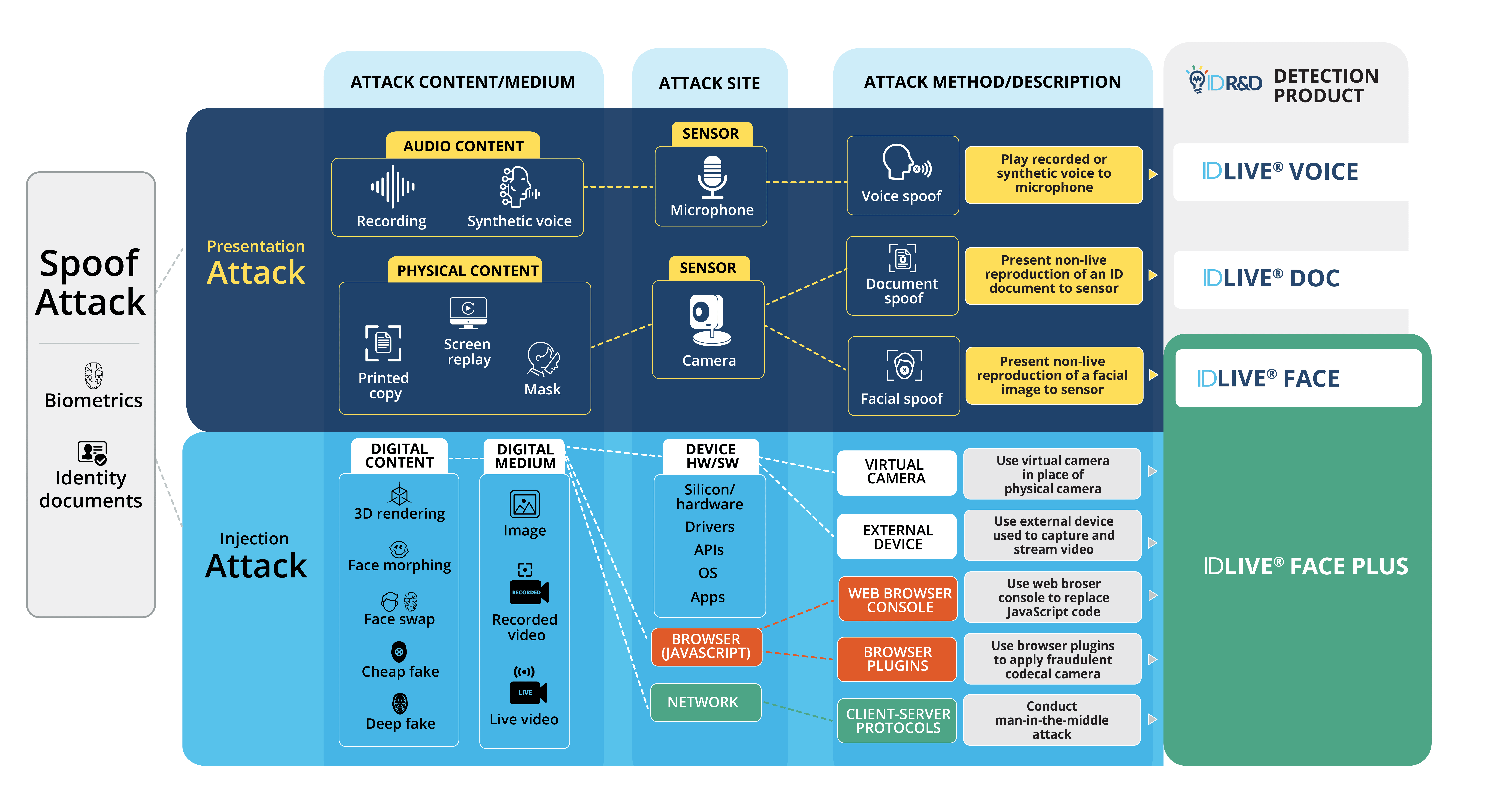








 The technology behind liveness detection is based on the recognition of physiological information as a sign of life. Historically, liveness algorithms have been
The technology behind liveness detection is based on the recognition of physiological information as a sign of life. Historically, liveness algorithms have been 

